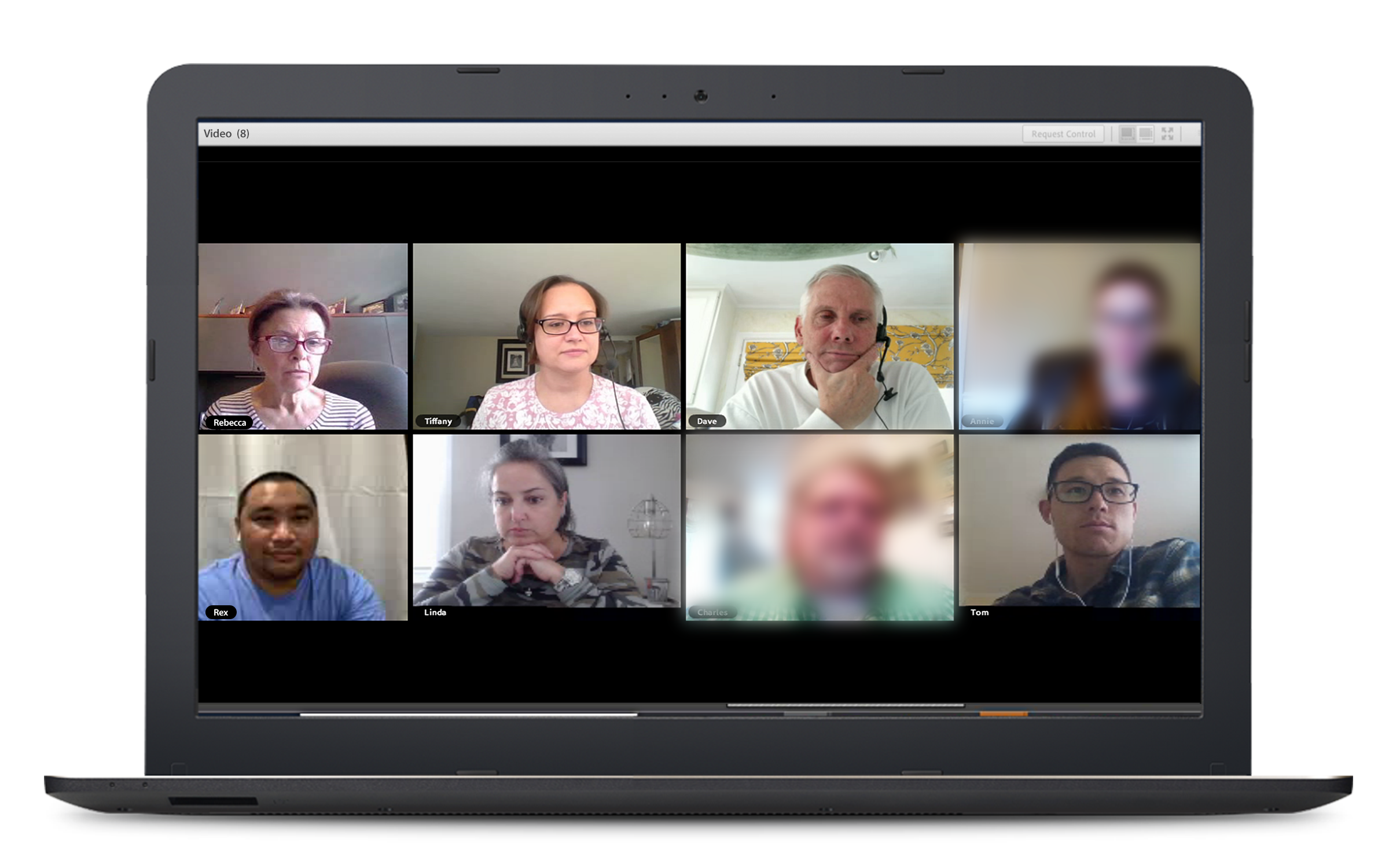
We take privacy and security seriously, and we know how important it is to deal with sensitive information. Civicom has a Face Blurring feature that you can use on your mock jury trials, so the jurors’ identities are protected. This feature lets you edit or blur our respondents’ image so that they are not recognizable.
Security
Security Measures

Audio Masking
Protecting sensitive information and confidential topics is important. As a global leader in facilitating online research groups, we can help you keep your participants’ identities confidential. Our Audio Masking Service can temporarily alter the voices of the online mock jury trial participants to keep their identities safe.

Data Encryption
We not only protect the data that is stored in our servers, but those that are in transit as well. Our Network Encryption Policy requires the use of cryptography to protect data packets coming to and from our system. All devices connecting to our network are subject to review and authorization is required before they are permitted to connect to our system.

Data Transfer
While our platforms provide secure storage and transfer of data, we understand that certain limitations are placed on data transfers due to strict company guidelines. We fully support the usage of specific file sharing systems preferred by clients.
We Take Security Seriously
Our secure service handles the privacy of your information
with utmost confidentiality and security.
We go to great lengths to ensure this is a priority throughout our organization. Our “culture of confidentiality” has four components:
- Processes
- Technology
- Legal Measures
- Independent Compliance Audit
Processes
Oath of confidentiality. Employees are required to say an oath of confidentiality quarterly, as a reminder of the personal responsibility to safeguard all data and PII and to follow required protocols..
Password-protected and limited-access accounts. Transcripts and audio files can only be accessed by transcriptionists to whom they are assigned. Login credentials are unique and can only be accessed by the Chief Confidentiality Officer. Our secure proprietary platform, TranscriptionManager, ensures files are only visible and accessible to the assigned team.
Limited file storage time. Transcripts and audio files are removed from our secure proprietary platform, TranscriptionManager once the project has been completed and delivered to the client. No one can access client files without appropriate security clearance.
Confidentiality process oversight manager. A Chief Confidentiality Officer is responsible for ensuring company-wide adherence to all four “culture of confidentiality” components.
Technology
Secure file deletion. When transcripts and audio files are deleted, they are purged according to current security standards to remove artifacts and the possibility of recovery.
Abnormality alerts. In the event unusual activity or unauthorized access to platforms is detected, exception reports are generated to immediately notify our Information Security team.
Biometrics, physical security. Entry and exit to and from the transcription room is restricted to authorized personnel We enforce data leak prevention policies such as paperless operations.
Legal Measures
All employees sign confidentiality/non-disclosure agreements at the start of their employment to legally bind them to protecting the confidentiality of client information. Agreements promise criminal litigation in cases where a violation is intentional or the result of gross negligence. Copies of this confidentiality statement are available on request.
Independent Compliance and Control Audit
An independent accounting firm annually audits the company’s adherence to confidentiality procedurestogether with the appropriateness of security controls , and provides a report. This is a self-imposed discipline which is designed to keep us on track, to continuously improve security as new threats emerge, and reassure our clients that these measures are more than just words.
Data security and confidentiality of information is our priority. Your files are protected at all times.
Choose Mock Jury Trials Online
Our services are tailored to meet any of your mock jury trial needs. From our proprietary audio conferencing technology, to our project curation system, our team of well-trained technicians will be with you every step of the way.